What Are Fullz - How Do Fullz Work?
What Are Fullz?
Fullz is a term used by criminals to describe sets of stolen personal information that can be used to impersonate someone or to use their bank cards.
Simply put, fullz are stolen identities or stolen credit card information.
https://discreetpeople.com/product-category/other/buy-cvv-fullz-online/
The word comes from the word “full” in the sense of “full data” or “full credentials” and encompasses all the information a fraudster needs in order to impersonate someone to defraud a company, steal directly from the victim, or conduct illegal activity that will be attributed to the victim if they are caught.
How Do Fullz Work?
Fullz can be acquired in several ways, including:
- Phishing and spear phishing: The victim is convinced they are sharing their passwords and/or other information with a legitimate company they trust.
- Bought on the dark web: Fullz are readily available to buy from other criminals, usually in bulk. Sourced from data breaches and elsewhere. These long lists will require card testing and other tests to identify which are live fullz.
- Rented out from ID mules: Fullz can be rented out on a temporary basis.
- Card skimming: Payment fullz can be obtained using devices such as ATM skimmers and other methods of stealing card information.
- Account takeover: Covert takeover of personal email or other accounts.
- Physical theft:By stealing someone’s physical documents or cards – and assuming they do not realize and/or cancel it.
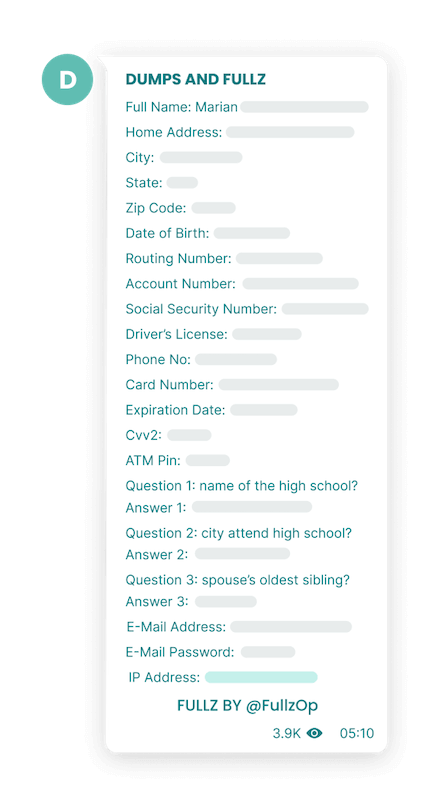
Typically, an ID fullz package contains:
- The victim’s full name
- The victim’s address
- The victim’s date of birth
- The victim’s social security number (or ID number, passport number, etc.)
- Other data, e.g. the victim’s email address (and sometimes their password)
The total cost of identity theft in 2020 was USD 56bn, per Javelin research, while Security Magazine reports that each fullz record averages USD 8 to purchase.
Meanwhile, a credit card fullz includes:
- Cardholder’s name
- Billing address
- CVV code
- Credit card number
- Expiry (and issue date where applicable)
See How to Fight Fullz Fraud
Fullz assist fraudsters in a large variety of fraud types. In order to avoid them, you need a strong, real-time fraud detection & prevention solution. Learn more about how these work.
According to 2021 reports, a criminal who wants to buy credit card fullz will pay anywhere from USD 0.11 to USD 986, depending on the type of card and how comprehensive the information is.
What Is a Dead Fullz?
Dead fullz are essentially data packages that are no longer valid because one or more essential pieces of information have changed.
This can happen deliberately, because the victim has realized their personal information and credentials have been compromised, or accidentally – for example, when someone has died.
Dead fullz can no longer be exploited for most purposes; they might briefly work but even the most rudimentary of anti-fraud protocols will catch the attempt and reject it. However, these are still useful for certain applications – for instance, opening a bank drop with certain banks.
How Are Fullz Used? Fullz Use Examples
Just a few common examples of fullz-related criminal activity are:
- Loan fraud: Fraudsters apply for payday and other types of loans
- Credit card fraud: They take full control of the card and mass purchase items or steal money from the account (potentially via money mules)
- Medical identity theft: To file insurance claims or apply for prescription drugs
- Synthetic identity fraud: Synthetic IDs combine fullz and criminal-generated information to try and bypass anti-fraud checks
- Tax refund scams: These defraud the person whose data is in the fullz, using the fullz information to convince them they are the tax authorities
- Bank drops: The ID can be used to open a bank drop account
- Subscription fraud: Criminals set up mobile subscriptions to acquire expensive smartphones and tablets, which they then resell
- Buy now pay later schemes:Fraudsters set them up, receive the item and never pay, affecting both the merchant’s revenue and the victim’s credit score
- Account takeovers: The victim’s account is taken over using the fullz information – from bank accounts to email accounts and beyond, this can also affect the organization who owns or manages the account, in addition to the victim
In essence, all identity theft fraud and all impersonation fraud uses fullz – as does all card-related fraud when it comes to carding fullz.
Where KYC verification protocols are used, fraudsters will attempt to use fullz to evade detection. And, the more comprehensive the information in each fullz, the more likely they are to succeed.
Lastly, we should note that fullz packages are also increasingly used in bot attacks.
How Does the Use of Fullz Impact Businesses?
The wide and diverse applications of fullz mean that most public-facing businesses with a remote or online element are susceptible to one type of fullz related fraud or another.
- Banking and insurance organizations can be targeted through bank drop creation, fraudulent credit card applications, and insurance fraud.
- Ecommerce businesses can find themselves caught up in carding, prepaid cards or chargeback fraud, among others.
- Because payment gateways deal with payment cards, all card-related fraud affects them – more rarely, the fraudster could even attempt to impersonate a merchant, depending on the fullz.
- Applications for loans are the main method fullz are used against online lending companies – the account will then default.
- In the highly competitive field of iGaming and gambling, fraudsters use fullz for affiliate fraud, matched betting, money laundering etc.
The above list is by no means exhaustive. Businesses of all sizes are encouraged to speak to fraud fighting and cybersecurity experts in order to identify the risks that apply to them in particular from the use of stolen credentials, as well as the best way to mitigate against them.
How to Avoid Fullz Fraud
As fullz fraud is basically used to enable a wide range of criminal, scammer and fraudster activity, protecting one’s company and reducing fraud rates comes from implementing a strong, flexible and comprehensive anti-fraud strategy.
The most efficient anti-fraud platforms will learn from each organization’s incident history as well as from incidents in their general field and locale, defining rules that are suitable for the organization, correspond to its risk tolerance, and can be suitably amended as the threat landscape changes.
Analysts can also take some time to look into the dark web for research purposes. There are other monitoring services available online to uncover whether or not a customer’s details have been included in a leaked fullz, which can be a clear signifier of fraud.
For the public, not becoming a victim of fullz involves following best cybersecurity practices, such as using multi-factor authentication and strong passwords.
However, organizations and merchants can also run campaigns to educate their users and buyers – to help themselves, too, since this can be a CSR initiative that improves their public image and earns them some publicity.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
.png)
About | Terms | Privacy | Support

© 2008 - 2023 Kuntal.Org Inc... All Rights Reserved



